Server architecture refers to the design and structure of server systems, encompassing hardware, software, network configuration, and other components. It determines how a server functions and delivers services to numerous users or devices across a network. This design is crucial in modern computing, influencing a server’s performance, reliability, and scalability.
This article will explore the most prevalent model, client-server architecture, discussing its key components and functionalities. We will also briefly introduce other server architecture types and discuss key considerations for building efficient server systems.
1. What is Client-Server Architecture and Why Does It Matter?
In a client-server architecture, a “client”, also known as a “host”, is any computer or device that requests services or information from a server. This can range from laptops and smartphones to IoT devices. Conversely, a “server” is a remote computer designed to provide access to data, applications, and other services. These are often powerful machines, either physical or virtual, handling tasks like email, web hosting, and database management.
“Client-server architecture” itself is a computing model that divides tasks and workloads between these clients and servers, whether they reside on the same network or are linked remotely. This division of labor is fundamental to modern computing. It brings a higher processing level to empower workstations or workgroups, improve remote network management, and facilitate complex business operations.
2. How Does Client-Server Architecture Work?
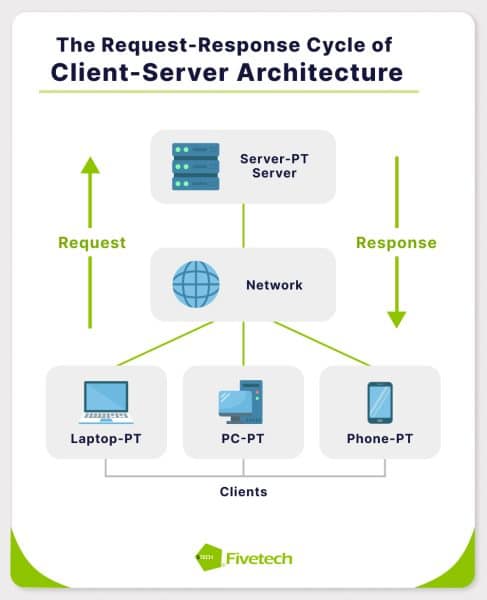
Client-server architecture operates on a request-response cycle. It begins with a client device initiating a request for specific data or a service. This request is transmitted over a network, such as the internet or a local area network, to a designated server.
The server then receives and processes this request. This processing may involve accessing databases, running applications, or performing other necessary operations to fulfill the client’s needs. Once the server has processed the request, it sends the requested data or the result of the service back to the client in the form of data packets.
The client then receives and interprets this response, presenting the information to the user. This continuous exchange of requests and responses forms the basis of client-server communication.
3. What are the Key Components of Client-Server Architecture?
The key components of server architecture include, but are not limited to, the hardware, software, operating system, networking infrastructure, and security mechanisms.
3.1. Server Hardware
Server hardware refers to the physical components that make up a server, establishing its computing power, storage capacity, and overall performance. Key hardware include:
- The server racks and chassis that house all the equipment
- The central processing unit (CPU) which processes instructions and executes tasks
- The random access memory (RAM) which stores temporary data for ongoing tasks
- Storage devices like hard drives and SSDs that save permanent data
- Network interface cards (NICs) for network connectivity
- The motherboard which connects all components
Another important component within the server hardware is the fastener. It is crucial to use high-quality fasteners to maintain the stability and reliability of the entire physical infrastructure. As such, operators may choose fasteners from brands offering specialized solutions for server hardware like Fivetech.
For instance, captive screws enable quick installation and prevent screws from falling off during operation; spring locks provide secure rack and chassis installation that resist loosening from vibrations; M.2 latches allow tool-less installation for delicate SSD cards within the motherboard to prevent damage from overtightening; while rotate ejectors simplify server hardware maintenance by facilitating effortless operation of heavy chassis.
3.2. Server Software Stack
The software stack is the installed components within the server. It determines the type of service delivered by the server and provides the functionality required by client applications. Examples include:
- Web server software, like Apache or Nginx, which handles HTTP requests
- Application server software, such as IBM WebSphere or Python with Django frameworks, that hosts and executes business logic
- Database server software, like MySQL or PostgreSQL, which manages data storage and retrieval
- Caching mechanisms, such as Redis or Memcached, which improve performance by storing frequently accessed data
3.3. Operating System (OS)
The operating system (OS) manages and coordinates server resources to handle client requests and ensure the smooth operation of server software. Common server OS examples include Microsoft Windows Server, various Linux distributions (like Ubuntu Server, CentOS, and Red Hat Enterprise Linux), and Unix-based systems (like FreeBSD and Solaris).
Unlike personal computer OSs focused on single-user interaction, server OSs are designed to handle multiple concurrent users so that they can manage vast amounts of data efficiently, prioritize robust security measures, and maintain uninterrupted operations for critical services.
3.4. Networking Infrastructure
Networking infrastructure acts as the communication interface, connecting the server to clients and potentially other servers within a network to enable data exchange and service delivery.
Key aspects of networking infrastructure include the network topology, which defines the physical or logical arrangement of network devices (e.g., star, mesh, bus), and network protocols, which are sets of rules governing data transmission (e.g., TCP/IP, HTTP).
3.5. Security Mechanisms
Security mechanisms are set up to protect the server and the sensitive data it manages. Examples of security mechanisms include:
- Firewalls that control network traffic
- Access controls that restrict user privileges
- Encryption which scrambles data to protect confidentiality
- Intrusion detection systems which monitor for malicious activity.
These measures safeguard against unauthorized access, data breaches, and other security threats.
4. What are the Pros and Cons of Client-Server Architecture?
This section will discuss the main advantages and disadvantages of the client-server architecture model.

4.1. The Advantages of Client-Server Architecture
Client-server architecture offers several significant benefits for organizations:
- Centralized Data Control and Management: This simplifies administration, ensuring data consistency across the network and streamlining the implementation of updates.
- Cost Efficiency: Although initial investments may be higher, simplified management leads to long-term cost savings. Moreover, Client-server architecture has lower maintenance costs than decentralized systems, as updates and maintenance are performed on the server rather than individual client machines.
- Improved Resource Sharing and Utilization: Clients can access shared server resources, leading to more efficient use of hardware and software. The emergence of virtualization and cloud computing also further boosts the advantages of resource sharing for greater accessibility.
- Scalability and Flexibility: Allows for load balancing by distributing workloads across multiple servers to prevent overload. Operators can also independently scale client or server capacity to meet changing demands.
- Simplified Data Recovery: The centralized system facilitates easier data recovery in case of failures and significantly reduces data replication to ensure data integrity.
4.2. The Disadvantages of Client-Server Architecture
The client-server architecture presents some vulnerabilities to issues such as:
- Single Point of Failure: A server outage will disrupt service for all clients, as the server is the central hub of the entire system.
- Malware: If the server is compromised by malware like viruses, Trojans, or worms, connected clients are at high risk of infection.
- Denial of Service (DoS) Attacks: Servers are susceptible to DoS attacks when a malicious party floods the system with massive volume of requests. This can overwhelm the server with traffic, causing system failure and disrupting service for all clients.
- Phishing Attacks: The system is vulnerable to phishing attacks, aimed at stealing user credentials.
- Man-in-the-Middle (MITM) Attacks: This is where attackers intercept and potentially modify communication between clients and servers.
- Data Packet Manipulation: Data packets transmitted across the network can be spoofed or altered, causing data inconsistency.
- Server Overloading: If the server experiences heavy client traffic which exceeds its maximum capacity, it may overload, resulting in performance degradation.
Hence, it is important to implement comprehensive security measures to prevent these risks.
5. Other Types of Server Architecture Models
Beyond the client-server model, there are several other common server architecture configurations, including:
- Peer-to-Peer (P2P) Architecture: It establishes direct connections between devices (peers), each acting as both client and server, sharing resources without a central authority. This offers simplicity in setup and resilience against single points of failure. The downside is it lacks centralized management so security can be inconsistent and performance can degrade with many users.
- Distributed Architecture: It employs multiple geographically dispersed servers working collaboratively. This distributes workload, improving performance and providing fault tolerance—if one server fails, others can take over. However, it introduces challenges in data consistency, synchronization, and overall management.
- Microservices Architecture: applications into small, independent services, each responsible for a specific function, communicating via APIs. This approach enhances development agility, scalability as individual services can be scaled as needed, and fault isolation since a failure in one service doesn’t necessarily bring down the whole application. Nevertheless, it is complicated in terms of inter-service communication, deployment, and overall system monitoring.
- Cloud Architecture: It leverages remote servers accessible over the internet to provide on-demand computing resources. Cloud models can be public, private, or hybrid, each with varying levels of control and security. This offers high scalability, flexibility, and cost-effectiveness by eliminating the need for extensive on-premises infrastructure. Yet, cloud solutions rely on internet connectivity and can raise data privacy concerns, making it unstable when not managed properly.
The server architectures mentioned above are all applied in high-performance computing, but they are rarely used in isolation. Instead, they are often integrated into heterogeneous computing clusters, functioning as building blocks or foundational infrastructure for demanding applications.
6. Key Considerations in Designing Server Architecture

Designing a robust server architecture requires careful consideration of several key factors:
- Load Balancing: It is essential for distributing incoming network traffic and workloads across multiple servers. This prevents any single server from becoming overloaded, ensuring consistent performance and responsiveness for all users. Effective load-balancing strategies contribute to improved resource utilization and prevent bottlenecks.
- Scalability: It addresses the system’s ability to handle increasing demands as the user base or data volume grows. This can be achieved through vertical scaling (upgrading existing server hardware) or horizontal scaling (adding more servers to the system). A scalable architecture ensures that the system can adapt to changing needs without significant performance degradation.
- Fault Tolerance: This is essential for minimizing downtime and ensuring continuous service availability. It involves implementing redundancy for hardware components, power supplies, and network connections, as well as failover mechanisms, allowing the system to continue operating even if one component fails.
- Cost Efficiency: Designing an efficient architecture can minimize hardware investments, reduce energy consumption, and streamline maintenance processes. This can involve using virtualization technologies, cloud services, and optimizing resource allocation.
- Efficient Monitoring and Management: This is vital for maintaining server health and performance. Implementing robust monitoring tools allows administrators to track key metrics, identify potential issues proactively, and optimize resource usage. Automated management tasks, such as backups and updates, further contribute to efficient operations and reduce administrative overhead.
By carefully addressing these factors, organizations can build server architectures to meet evolving needs and ensure smooth operation.
7. Future Trends in Server Architecture
The future of server architecture is being shaped by several key trends. These trends are converging to create server architectures that are more distributed, intelligent, and environmentally conscious
For example, edge computing and decentralization are gaining momentum as data processing moves closer to the source of data generation, reducing latency and bandwidth demands. This involves deploying smaller, localized servers at the “edge” of the network, enabling faster response times for applications like IoT and real-time processing.
This trend is further amplified by the rise of Edge AI, where AI algorithms are executed directly on user devices like smartphones, wearables, drones, AR/VR devices, vehicles, and more. This shift reduces reliance on centralized cloud servers and enables faster, more secure, and efficient data processing at the device level to create a better user experience.
Furthermore, AI and machine learning integration are driving the development of specialized hardware and software within server architectures. This includes the use of GPUs, FPGAs, and other accelerators optimized for AI workloads, enabling servers to handle complex computations for tasks like natural language processing, image recognition, and predictive analytics.
Additionally, there’s a growing emphasis on sustainable and energy-efficient architectures. This includes designing servers with lower power consumption components, implementing advanced cooling systems (like liquid cooling), and optimizing power management strategies. This focus is driven by both environmental concerns and the increasing costs of energy consumption in large data centers.
7.1. The Role of Fastener Components in Server Architecture Innovation
Fasteners within the server not only hold components together but also directly impact crucial aspects like space utilization, ease of assembly, and overall system reliability. As server designs evolve towards miniaturization and modularity, the role of innovative fastening solutions becomes even more critical.
Fivetech, specializing in these components, offers products that directly support these advancements. Namely, the Double M.2 board latch enables simultaneous installation of two M.2 SSDs without the need for tools, maximizing storage density within limited space. This directly contributes to building smaller, more powerful servers.
Moreover, Fivetech’s Latch Ball Lock facilitates modular design with its quick-release mechanism and hold-open functionality. Its protruding ball design also enables more effective panel fastening to prevent loose components, while the one-finger operation ensures ease of use, even in confined server environments. This allows for quicker server assembly, maintenance, and upgrades, directly supporting scalable server deployments where components can be easily added or replaced as needed.
8. Reliable Server Hardware Components by Fivetech
Fivetech is a leading provider of innovative and reliable fastening solutions for various industries, including server hardware. We offer an extensive catalog of components, from quick-release screws and handles to specialized selections like PCB standoffs, M.2 board latches, and latch locks — all ISO-certified and RoHS-compliant.
On top of that, Fivetech is committed to quality, innovation, and customer satisfaction, providing stable large-scale production, timely delivery, and customization services to meet specific application needs.
Explore Fivetech’s comprehensive range of server hardware solutions today to enhance the reliability and efficiency of your server infrastructure.